Towerwall's InfoSec Blog
Content Type
- Enterprise (299)
- cannabis (258)
- cybersecurity (134)
- Information Security (124)
- Compliance (104)
- Data Security (100)
- ransomware (99)
- Security (98)
- Security Threat (91)
- Phishing (90)
- cybercriminals (84)
- security policy (84)
- malware (79)
- information security tips (74)
- security software (71)
- Compliance & Privacy (70)
- Data Breach (70)
- Application Security (69)
- Security Program (67)
- Security Regulations (67)
- network security (66)
- Mobile Security (63)
- Security Services (60)
- Hackers (59)
- Cloud Security (55)
- Security Alert (55)
- penetration testing (55)
- GDPR (51)
- COVID-19 (50)
- HIPAA (50)
- PCI (46)
- security research (45)
- Data Privacy (44)
- cyber-attack (44)
- Security Partners (41)
- Events (37)
- Big Data (30)
- Mobile Apps (30)
- Mobile Devices (29)
- Mobile Protection (24)
- Business Continuity (22)
- credit card security (22)
- Fractional Chief Information Security Officer (CIS (19)
- Webinar (19)
- Information Security Summit (18)
- Michelle Drolet (18)
- Social Engineering (18)
- Worcester Business Journal (18)
- BYOD (16)
- financial security (16)
- Sophos (15)
- Towerwall (15)
- threat landscape (15)
- vCISO (15)
- cloud services (14)
- endpoint security system (14)
- Internet of Things (13)
- passwords (13)
- vulnerability management (13)
- CCPA (12)
- 10 Things I Know (11)
- Web Browser (11)
- Gap Assessment (10)
- Virtual CISO (10)
- cannabis compliance (10)
- Assessment (9)
- Web Application Firewall (9)
- web server (9)
- web users (9)
- CISO (8)
- T-Mobile (8)
- cannabis security (8)
- iPhone (8)
- General Data Protection Regulation (GDPR) (7)
- Government Compliance Regulations (7)
- MassBay Community College (7)
- SnoopWall (7)
- Tablets (7)
- Web Storage (7)
- phishing attacks (7)
- software updates (7)
- BrightTalk (6)
- IoT security (6)
- Microsoft (6)
- meetup (6)
- Android (5)
- Apple (5)
- Encryption (5)
- Equifax (5)
- European General Data Protection Regulation (GDPR) (5)
- IT Infrastructure (5)
- InfoSec at Your Services (5)
- InfoSec at Your Services Meetup (5)
- IoT (5)
- Armis (4)
- Coronavirus (4)
- Forbes Technology Council (4)
- ID Theft (4)
- Mac (4)
- NIST (4)
- NetworkWorld (4)
- OWASP (4)
- Varonis (4)
- email scam (4)
- iOS (4)
- 2016 Outstanding Women in Business (3)
- AT&T (3)
- Becker College (3)
- Breach Response (3)
- California Consumer Privacy Act (CCPA) (3)
- CannaCare (3)
- Cryptolocker (3)
- Cybersecurity Framework (3)
- DROWN (3)
- GRC (3)
- Heartbleed (3)
- ISSA (3)
- ISSA New England (3)
- Linkedin (3)
- Massachusetts (3)
- Middlesex Savings Bank (3)
- Penetration Tests (3)
- Third-party Vendor (3)
- Verizon (3)
- Wireless (3)
- Yahoo (3)
- Zero Trust (3)
- artificial intelligence (3)
- cybercrime (3)
- iOS update (3)
- internal emails (3)
- medical marijuana (3)
- software systems (3)
- #WBJITFORUM (2)
- #summitbuzz19 (2)
- 4E Methodology (2)
- AMG (2)
- AlienVault (2)
- Allegro MicroSystems (2)
- Amazon (2)
- Banking Cannabis (2)
- Bluetooth (2)
- Boston (2)
- Botnet (2)
- Breach Prevention (2)
- Budget (2)
- CDW (2)
- CEO (2)
- Cache (2)
- Candy Alexander (2)
- Center for Internet Security (CIS) (2)
- Community Involvement (2)
- CryptoWall v3 (2)
- Cyber Security (2)
- Cyber Security Career Lifecycle ( CSCL ) (2)
- CyberSN (2)
- Darktrace Ltd (2)
- Data breaches (2)
- Educate (2)
- Endpoint Protection (2)
- Establish (2)
- FBI (2)
- Facebook (2)
- Firefox (2)
- Fortinet (2)
- Framingham (2)
- Gary Miliefsky (2)
- General Data Protection Regulation (2)
- Gmail (2)
- Hack (2)
- ISACA (2)
- ISO 27001/2 (2)
- Incident Response Plan (2)
- Information Security Summit 2016 (2)
- Information Security Summit 2017 (2)
- Information Systems Security Association (ISSA) (2)
- Intercept X (2)
- Internet Explorer (2)
- Linux (2)
- Michael Lyons (2)
- Office (2)
- Open Web Application Security Project (OWASP) (2)
- Outlook (2)
- PhishMe (2)
- Qnext/FileFlex (2)
- RSA (2)
- Regulated Industries (2)
- Remote Workforce (2)
- Risk Management (2)
- SOX (2)
- SSL (2)
- Secure Development Life Cycle Plan (SDLC) (2)
- Security Awareness Training Program (2)
- Security BSides Boston 2016 (2)
- Shockwave. Internet Explorer (2)
- Smart Device (2)
- Smart Home (2)
- Smartphone (2)
- Sophos Intercept X (2)
- Training (2)
- Twinstate (2)
- Twitter (2)
- Wearables (2)
- Windows (2)
- bot-infected (2)
- cisco (2)
- cybersecurity trends (2)
- edge-cloud architecture (2)
- employee (2)
- endpoint detection (2)
- hackings (2)
- infected computer (2)
- infected phone (2)
- malwarebytes (2)
- medical cannabis (2)
- password (2)
- password protection (2)
- scammers (2)
- spear phishing (2)
- third party applications (2)
- two-factor authentification (2)
- vulnerability scanning (2)
- #brainbabe (1)
- #summitbuzz18 (1)
- 20 Critical Security Controls (1)
- 2017 Community Leadership Breakfast (1)
- 2017 Power 30 Solution Providers (1)
- 2018 (1)
- 2019 (1)
- 3D Printing (1)
- AOL (1)
- APT (1)
- AT&T Alien Labs Open Threat Exchange (OTX) (1)
- ATM (1)
- Ad Threats (1)
- Add-ons (1)
- Advanced Threat Detection (1)
- Alien Vault (1)
- Anti-Phishing Working Group (APWG) (1)
- Apple Pay (1)
- Appliance Analysts (1)
- Application Software Security (1)
- April Fools (1)
- BSides Boston (1)
- Bash (1)
- Big Switch (1)
- Breach Response Plan (1)
- Bro (1)
- Bugcrowd (1)
- CES (1)
- CFO (1)
- CIA (1)
- CIO (1)
- CIS Controls (1)
- CIS Controls 16 (1)
- CIS Controls 17 (1)
- CNBC (1)
- COSO Cube (1)
- CPEs (1)
- CRNtv (1)
- CSF (1)
- CTO (1)
- CYBER (1)
- Cash (1)
- Channel Partners (1)
- Chief Security Officer (1)
- China hack (1)
- Chrome (1)
- Clickbait (1)
- Community Leadership (1)
- Compliance and Regulations (1)
- Conference (1)
- Conficker (1)
- Consumer Privacy Rights and Enforcement Act (1)
- Cookies (1)
- Corporate Security (1)
- Counterintelligence Program (1)
- CreditDonkey (1)
- Crisis Response Plan (1)
- Critical Security Controls (CSC) (1)
- CryptoWall (1)
- Cumberland County College's 2017 Business Leaders' (1)
- Cyber Defense Magazine (1)
- Cyber Resilience (1)
- Cyber Security Leader 2016 (1)
- Cyber Security Leader for 2016 (1)
- Cyber Security education (1)
- Cyberattack (1)
- DDoS attacks (1)
- DOM (1)
- DPO (1)
- DRIDEX botnet (1)
- DROWN vulnerability (1)
- Dark Reading (1)
- Darkode (1)
- Data Loss Prevention (DLP) (1)
- Data Protection Officer (1)
- Deidre Diamond (1)
- Democratic Party (1)
- Department of Consumer Affairs (1)
- DevOps (1)
- Diana Kelley (1)
- Dr. David Podell (1)
- Drug Policy Alliance (1)
- EDR (1)
- EMV credit cards (1)
- ETag (1)
- EU Data Protection (1)
- EU legislation (1)
- Enforce (1)
- Entrepreneurship (1)
- European Data Protection Board (EDPB) (1)
- European Union (1)
- Evaluate (1)
- FCC (1)
- FISMA (1)
- FREAK (1)
- FTG (1)
- Fingerprinting (1)
- Flash Cookies (1)
- Forbes (1)
- Foundation for MetroWest (1)
- Fox 25 (1)
- Framework (1)
- Free Security Tools (1)
- GDPR Fines (1)
- GHOST (1)
- GNU Bash Remote Code Execution Vulnerability (1)
- Gartner (1)
- General Data Protection Legislation (GDPR) (1)
- Gift Cards (1)
- Gigamon (1)
- Google (1)
- Google Wallet (1)
- GovConnection (1)
- HTML (1)
- HTTP (1)
- HTTPS (1)
- Have I Been Pwned? (1)
- Health Insurance Portability & Accountability (1)
- Hidden URLs (1)
- IAST (1)
- IBM (1)
- IE (1)
- ISSA International Awards (1)
- ISSA International Conference (1)
- ISSA New England Chapter Meeting (1)
- IT Support (1)
- IT Systems (1)
- IT departments (1)
- Imperva (1)
- Imperva Scuba Database Vulnerability Scanner (1)
- Incident Response and Management (1)
- InfoSec at your Service (1)
- Information Security Summit Scholarship (1)
- Information Systems Security Association (1)
- Infraguard (1)
- Interwork (1)
- Intrusion Detection Systems (1)
- Iowa Voting App (1)
- Java (1)
- Jeffrey Davis (1)
- Juniper (1)
- Juniper Netwroks (1)
- KISSmetrics (1)
- Kali Linux (1)
- Kismet (1)
- Kmart (1)
- KnowBe4 Phish-prone (1)
- KnowBe4 RanSim (1)
- Known vulnerabilities (1)
- KrebsonSecurity (1)
- LSO (1)
- Legal weed (1)
- LogRhythem (1)
- LogRhythm NetMon Freemium (1)
- MJ Freeway (1)
- MaaS (1)
- Mac OSX (1)
- Malicious software (1)
- Malvertising (1)
- Mark Zuckerberg’ (1)
- Mary Shia (1)
- Mass Bay Community College (1)
- Mass Department of Public Health (1)
- MassBay (1)
- MetroWest (1)
- Microsoft NERD (1)
- Misconfigurations (1)
- Multi-Stage Attacks (1)
- NFC (1)
- NIST Cybersecurity Framework (1)
- NIST Cybersecurity Framework (CSF) (1)
- NIST framework (1)
- Nadir Izrael (1)
- National Initiative for Cybersecurity Education (N (1)
- National Institute of Standards and Technology (NI (1)
- National Security Agency (NSA) (1)
- Near-Term ROI (1)
- Nigerian prince (1)
- OSSEC (1)
- Offensive Security (1)
- Open DLP (1)
- Open Source (1)
- Outstanding Women in Business (1)
- PIE (1)
- Patch (1)
- PayPal (1)
- Pcysys (1)
- PenTera (1)
- Penalties (1)
- Pinterest (1)
- Ponemon Institute (1)
- Ponemon Institute Data Breach (1)
- Portables (1)
- Pot Compliance (1)
- Private Browsing (1)
- Pseudonymization (1)
- Public Wi-Fi (1)
- Pwn2Own (1)
- Qualys (1)
- Qualys Cloud Platform Community Edition (1)
- Quizzes (1)
- RFID credit cards (1)
- Radio Entrepreneurs (1)
- Ransomware Protection (1)
- Red Team Exercises (1)
- Risk Management Strategy And Program (1)
- Romance Scams (1)
- SHA1 (1)
- SHI (1)
- SIMDA botnet (1)
- SPAM (1)
- SQL injection (1)
- SSLv2 (1)
- SSLv2 server (1)
- Safari (1)
- SamSam attack (1)
- Scams (1)
- Scholarship (1)
- Science and Technology Tagged With: cannabis compl (1)
- Secure Building (1)
- Securonix (1)
- Settings (1)
- Shellshock. Bash bug (1)
- Shortened URLs (1)
- Silicon Review (1)
- Smith & Wesson (1)
- Snort (1)
- Social Media (1)
- Social Phishing (1)
- Social Security Number (1)
- Sony (1)
- Sophos Intercept X for Mobile (1)
- Sophos SafeGuard Encryption 8 (1)
- Sophos XG Firewall Home Edition (1)
- Spear phishing emails (1)
- Special Publication 800-53 (1)
- Starbucks (1)
- State regulations (1)
- Stealthbits (1)
- Subject Access Request (SAR) (1)
- SuperCom (1)
- Syria (1)
- TCG (1)
- TCG Network Services (1)
- TLS (1)
- Target (1)
- Targeted Cyberattack (1)
- Tax (1)
- TechTarget (1)
- The Hawaii Dispensary Alliance (1)
- Third Party Outsourcing (1)
- Threat Intelligence (1)
- Title II of the Communications Act (1)
- Top Computer Security Blogs 2016 (1)
- Towerwall Security Alert (1)
- Towerwall in the News (1)
- Town Hall (1)
- Trend Mico (1)
- TrendMicro (1)
- Trends to Watch for in 2018 (1)
- Trojan-like Emotet (1)
- U.S. Department of Health (1)
- UPnP (1)
- USB (1)
- USM (1)
- Unified Security Management (USM) (1)
- Uniforms (1)
- Unix (1)
- Unsecured Wi-Fi (1)
- Unstructured Data (1)
- User behavior analytics (UBA) (1)
- VPN (1)
- Veeam (1)
- Virus (1)
- Vormetric (1)
- Vulnerability Management Plan (1)
- WannaCry (1)
- Whitelist (1)
- Whitepaper (1)
- Wi-Fi (1)
- Wikipedia (1)
- Wireless Access Control (1)
- Worcester Business Journal's IT Forum (1)
- WordPress (1)
- Xerox Corporation (1)
- Year in Review (1)
- Zero-Day Protection (1)
- Zero-day malware (1)
- Zero-trust networks (1)
- application testing (1)
- appsec (1)
- ata protection officer (1)
- auditing (1)
- authentication (1)
- behavior analytics (1)
- boston voyager (1)
- botnets (1)
- boundary defense (1)
- breach (1)
- business security (1)
- canna care (1)
- case study (1)
- certificates (1)
- cloud application security (1)
- cloud phishing (1)
- continuous data protection (CDP) (1)
- cyber defense (1)
- cyberattacks (1)
- cybersecurity professionals (1)
- dark web (1)
- darwin (1)
- darwin defense (1)
- data collection (1)
- data recovery capability (1)
- data recovery plan (1)
- data storage (1)
- database systems (1)
- device management (1)
- disaster recovery (1)
- eBay (1)
- endpoint visibility (1)
- firewalls (1)
- hacking (1)
- haveibeenpwned.com (1)
- high-profile data breaches (1)
- human error encryption (1)
- identification (1)
- independent testing (1)
- ito (1)
- lingo (1)
- machine learning (1)
- military (1)
- mobile malware (1)
- multifactor authentication (MFA) (1)
- open-source software (1)
- operationalizing cybersecurity (1)
- patch management (1)
- phishing attack (1)
- point-of-sale breach (1)
- pot dispensaries (1)
- private sector (1)
- protected health information (PHI) (1)
- public sector (1)
- quid pro quo (1)
- ransomware-as-a-service (1)
- remote browser isolation (RBI) (1)
- risk tolerance (1)
- routers (1)
- sandbox (1)
- secure configurations (1)
- security assumptions (1)
- security information and event management (SIEM) (1)
- small and midsize businesses (1)
- small to medium size enterprises (SMEs) (1)
- smart TV (1)
- smart fridge (1)
- smart-connected (1)
- software bugs (1)
- spambots (1)
- switches (1)
- tED Magazine (1)
- third-party partners (1)
- third-party social media plug-ins (1)
- trends (1)
- two-factor authentication (1)
- vulnerability (1)
- web application security (1)
- white market (1)
- zero-day (1)
5 Information Security Trends for 2016
Michelle Drolet
Online security trends continue to evolve. This year, online extortion will become more prevalent. We also expect that at least one consumer-grade IoT smart device failure will be lethal. Ransomware will make further inroads, since the majority go unreported. China will drive mobile malware growth to 20M, and cybercrime legislation will take a significant step towards becoming a truly global movement. Here are five information security trends on track for the New Year:
2 Minute Read
10 Things I Know About Business Security
Michelle Drolet
10. Everything is connected. As the Internet of Things adds more and more devices to our networks, it creates more doors and windows for cyber criminals. Keep them locked.
1 Minute Read

Join us for the ISSA New England Virtual Chapter Meeting - January 21, 2016
Michelle Drolet
The ISSA of New England's 2nd annual virtual chapter meeting will be on: Thursday, January 21 at 12:00 Noon. ( Yes, while you eat lunch you can join us online. ) Careers in Cyber Security is the theme of this meeting. The most pressing problem in security is for sure the lack of qualified people to fill the number of open roles. If you or your firm are looking for people to hire, this session is for you. If you are looking for a new and better role in 2016, this session is for you.
2 Minute Read
The Worst Hacks of 2015
Michelle Drolet
Hacking and data breaches weren’t just the norm, but they reached far and wide, hitting victims of all kinds, from regular consumers, to government employees, and even children and cheaters. It seemed like no one was spared. The Worst Hacks of 2015…drum roll please!
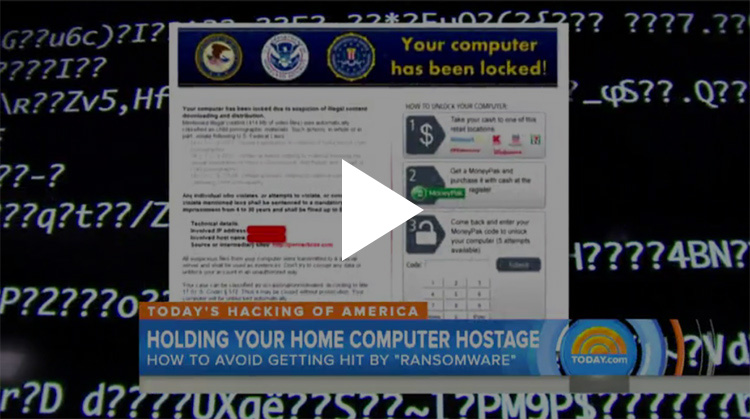
Ransomware Featured on the Today Show
Michelle Drolet
A "ransomware" segment was recently on NBC's Today featuring our security partner Sophos. To learn more about ransomware. click the thumbnail below:
Building malware defenses: Control email, web browsers, and ports
Michelle Drolet
Another staple in a series examining the Center for Internet Security's best practices. Our last article looked at applying Critical Security Controls 4, 5, and 6 to your organization, covering vulnerability assessment, administrative privileges, and audit logs. Now it’s time to move on to CSCs 7, 8, and 9. Email programs and web browsers are still the most common points of entry for attackers, too many companies have woefully inadequate malware defenses, and a failure to control ports andfalse
2 Minute Read
Applying more Critical Security Controls to your organization
Michelle Drolet
The last time we looked at how Critical Security Controls (CSC) can help you build your InfoSec framework, we covered getting a handle on your software and your hardware inventories. Today, we're going to discuss the importance of continually assessing and remediating vulnerabilities, keeping a tight control of administrative privileges, and monitoring your audit logs. These concepts are encapsulated in CSCs 4, 5, and 6. You should develop stringent policies, consider devoting resources tofalse
2 Minute Read
Towerwall Donates $7K to MassBay Foundation
Michelle Drolet
Originally posted on MetroWest Daily News. Towerwall, a Framingham-based network security and policy management company, donated $7,000 to the MassBay Foundation to sponsor student scholarships. Towerwall CEO Michelle Drolet, who is also a board member of the MassBay Foundation, presented MassBay interim president Yves Salomon-Fernandez, MassBay chief information officer Michael Lyons and MassBay vice president for institutional advancement and alumni relations Mary Shia with a gift of $7,000.false
1 Minute Read
Four Signs your mobile app may be at risk
Michelle Drolet
How can you make sure the mobile apps you access are secure? A security profile should be at the top of the developer’s list when compiling a mobile app but that’s hardly the case. That’s a pity, because building a profile is easier to do during the dev phase. Are most mobile apps putting your data at risk? Most likely so. According to the most recent report from Lookout, the number of Android devices affected by malware is more than 6 million. Luckily, there are telltale signs that indicate anfalse
2 Minute Read
The challenges of third-party risk management
Michelle Drolet
Vendors and other third parties should be treated with the same level of intense scrutiny as your own in-house risk compliance mandates. How seriously is your company treating the risk of a data breach? Have you done due diligence on all of your vendors and third-party partners? Cyberattacks can have a devastating impact in terms of reputation and customer trust. It takes time and resources to deal with the fall out. The true cost of a serious data breach is hard to calculate.
3 Minute Read